
Understanding cybersecurity work roles and job titles
By Frederick Scholl June 01, 2019

By Frederick Scholl June 01, 2019

The cybersecurity field is so broad that standardized work roles and job titles have yet to crystallize. I see huge variation across industry verticals and between public and private sectors. An important part of that is to better understand what types of jobs are available.
The Federal government has categorized cybersecurity jobs into the Cybersecurity Workforce Framework.1 This is a very comprehensive analysis of cybersecurity jobs that lists 52 Work Roles and work role descriptions. The document is important to read but has some shortcomings. For one, the designated work roles do not necessarily correspond to today’s job titles or even job listings. For another, Work Roles are listed that incorporate security tasks, but are not necessarily 100% engaged with security. For example, the NICE “Target Developer” does not have any listed jobs on Indeed. The NICE work role of “Software Developer” is too broad to align with specific cybersecurity jobs.
I analyzed the actual job titles and descriptions on www.indeed.com to find out what job categories are in demand now. (Another popular job board that could be used is www.simplyhired.com.) I didn’t start from a clean sheet, but rather started with the good listing of 35 cybersecurity job roles on www.cybersn.com. CyberSN is a cybersecurity staffing firm and their list of roles is the best practical one I have seen to date.
First, I scanned Indeed to look for all cybersecurity jobs listed. I found a total of 17,589 open now. This scan was based on everything that had the term “cybersecurity” in the title or job description. So, I did not count jobs such as “Software Developer”, unless the term cybersecurity appeared. Next, I searched, within that set of 17,589 jobs, to find jobs with specific terms in the listing title. Note that the actual offered job title might differ somewhat from the listing title. The specific terms I searched on came from CyberSN, from NICE and from my own observations of the listings on Indeed. I searched on 45 categories. My goal was to eliminate the miscellaneous category, but many jobs still fall outside the 45 specific categories I identified.
First let’s look at jobs that are “missing in action”. These are job categories that had only a few or no listings yet are popular in press discussions. Media coverage does not immediately translate into open positions.
Jobs Missing in Action
| Job Category | Number of Open Positions |
| Cryptography | 0 |
| Cryptanalyst | 0 |
| Staffing | 3 |
| Intrusion Detection | 6 |
| Awareness | 11 |
| Firewall | 15 |
| Malware | 34 |
| Reverse Engineer | 27 |
| Pen Tester | 58 |
What can we conclude from these numbers? First the demand for new crypto experts is zero! Unless quantum crypto comes into the fore, the golden age of crypto may be over. On the other hand, there are 2,284 open positions for “blockchain”, so applications of cryptography represent good opportunities. Second, staffing firms seem to be filled with labor; there are only so many cybersecurity professionals to be recruited! I believe this is a natural limit on the demand for staffing talent. I was surprised that “Intrusion Detection” jobs were low. “Intrusion detection” has been integrated into many security platforms. Similarly, these positions have become more general and likely moved into the security analyst and security engineer titles. Awareness was also surprisingly low, indicating that many firms are likely outsourcing their awareness needs, rather than having in-house trainers. Malware related positions (including reverse engineer) have a low demand, as attacks have made more use of stolen credentials. Finally, I was surprised that the number of pen tester openings was relatively low. This role is under pressure from potentially more effective bug bounty programs and breach and attack simulation tools.
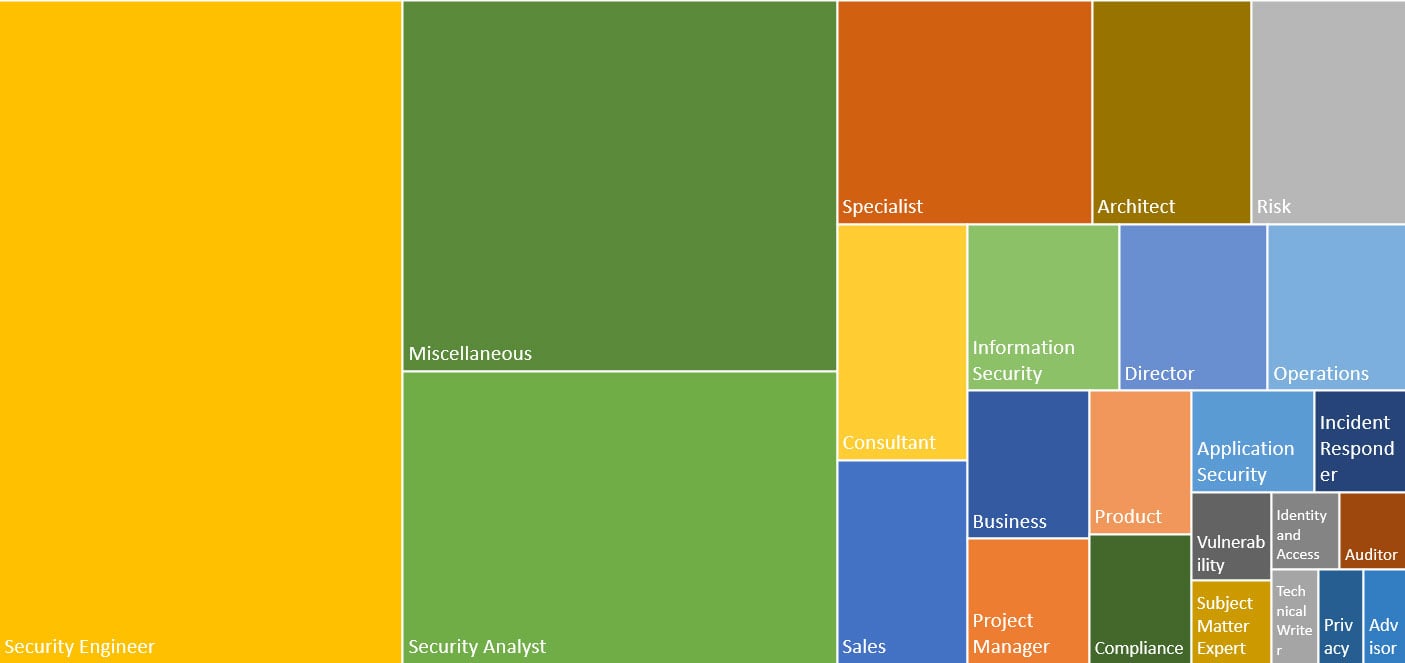
What about roles that are in demand? The demand for the top 24 roles is illustrated in the accompanying tile chart. Remember, this chart was obtaining by searching www.indeed.com for positions including the word “cybersecurity” anywhere in the listing AND the specific roles in the job title. Some observations: the miscellaneous category is the second largest. This attests to the fact information security is a broad discipline and intersects with many other areas. Regarding the other roles, I list each with my own comments gleaned from searching Indeed.
| Cybersecurity Role | Comments and Observations |
| Sales | Always needed in software, hardware and services |
| Project Manager | Without an effective PM, most security initiatives will fail |
| Technical Writer | Technical people do not like to write policies, procedures and standards, so interesting opportunity here, if you do |
| Security Engineer | Mostly involved with preventing breaches |
| Application Security | If you can code AND understand security risks, you will be employed for the foreseeable future |
| Security Analyst | Focused on detecting breaches and attack vectors |
| Incident Responder | Once an incident or event has occurred, appropriate response must be carried out |
| Auditor | Not in the security function; reports to internal or external audit |
| Vulnerability | Classical security role; with 16,500 vulnerabilities cataloged last year (2018), this is role is not going away soon |
| Architect | At the top of the cybersecurity food chain, one level below CISO |
| Privacy | Regulations like GDPR will make this role more important |
| Compliance | Meeting compliance requirements inside a security function is still a critical endeavor |
| Director | One step below CISO |
| Product | Product security is a critical function, if often overlooked job |
| Consulant | At a senior level, providing internal users good security recommendations |
| Operations | Security Operations Centers, internal or outsourced, are becoming popula |
| Information Security | Some government positions still use this older term |
| Business | More and more cybersecurity positions will move into business units |
| Specialist | Another term used in government agencies and their contractors |
| Identity and Access | Very important function within a cybersecurity portfolio |
| Subject Matter Expert | Technology role focused on security |
| Advisor | Another senior cybersecurity role |
| Miscellaneous | The large number in this category is indicative of the broad sweep of cybersecurity positions |
The way to use this information is to review these categories and determine which ones you might be interested in. Then search Indeed to ferret out the detailed job descriptions. Do you have the needed skills, knowledge and abilities? If not, set up a plan to acquire those job components. I highly recommend watching my interview with Quinnipiac’s Engineering School Director of Career Development, John Bau. This will show you how to use your acquired security skills, knowledge and abilities to make a career transition into cybersecurity.
For more information go to QU’s online programs.
1NIST Special Publication 800-181, NICE Cybersecurity Workforce Framework, August 2017.
Quinnipiac Today is your source for what's happening throughout #BobcatNation. Sign up for our weekly email newsletter to be among the first to know about news, events and members of our Bobcat family who are making a positive difference in our world.
Sign Up Now